 |
|
Home → News 2018 March
|
02.March.2018
SOPR #109
We have to acknowledge that cyber sovereignty is not only an important desire and topic in the P.R.China but also in Russia and Saudi Arabia, as well as the French Republic and most potentially in other countries.
In this relation, we already pointed out a disharmony between the
which demands that a solution must be found that is acceptable for both sides and therefore cannot solely be based on politics.
In addition, we observed ambitions of economic areas to become one of the world's main hubs for storing and processing big data or providing other services. For sure, these services make only sense when being integrated in our ON, OW, and OV respectively being Ontologic Applications and Ontologic Services (OAOS), which requires SOPR membership.
The two simple solutions suggested by us are that a government or the companies of a country
- 5. ring/ID space, including the common Internet and World Wide Web (WWW), and
- 6. ring/ID space (see the sketch given in the Ontonics Further steps of the 10th of July 2017),
where the individual states are already asserting their cyber sovereignty.
But we also recommended to remove restrictions related to world wide communication and publication, and do not want to make politics either.
So the main question is how to handle ID spaces and transitions between ID spaces in accordance with cyber sovereignty, which leads to further questions like the following ones:
No decision has been made.
03.March.2018
SOPR #110
We continued with the topic of cyber sovereignty (see also the issue #109 of the 2nd of March 2018 (yesterday)) and have developed another solution for reaching harmony in relation with Cyber Sovereignty (CyS) that could include the following rules (used acronyms Ontologic System (OS), Ontologic Net (ON), Ontologic Web (OW), Ontologic uniVerse (OV), IDentification space (ID space)):
- CyS.1.1.1 within its real area of sovereignty,
- CyS 1.1.2 in accordance with
- CyS.1.1.2.1 the local jurisdiction and
- CyS.1.1.2.2 international agreements,
and
- CyS.1.1.3 for a SOPR member who
- CyS.1.1.3.1 is a citizen of said SOPR member,
- CyS.1.1.3.2 has a domicile or permanent residence within the real borders of said SOPR member, and
- CyS.1.1.3.3 has a place of taxability within the real area of sovereignty of said SOPR member.
- CyS.1.2.1 the fourth SOPR member violates CyS.1.1 in relation with the access to the OS and the experience in the ON, OW, and OV of the second SOPR member, and
- CyS.1.2.2 the third SOPR member is within the real area of sovereignty of the first SOPR member.
- CyS.1.3.1 regulation of a crossing over one or more borders between ID spaces,
- CyS.1.3.2 control of an issued ID at a crossing over one or more borders between ID spaces, and
- CyS.1.3.3 management of a financial transaction over one or more borders between ID spaces
through the related ON, OW, and OV platforms.
Comments and exemplary scenarios to paragraph CyS.1.1:
(i) Only within the real borders of sovereignty of a first state and only for a first citizen from said first state the ID space can be regulated in accordance with the local jurisdiction of said first state and international agreements. This means that a second citizen from a foreign second state remains in her/his ID space and correspondingly gets the same access to the OS and enjoys the same experience in the ON, OW, and OV in accordance with the regulations of her or his second state even when being within the real borders of sovereignty of said first state.
For example, a citizen from the U.S.A. or a member state of the E.U. has the unrestricted access to the ON, OW, and OV, and enjoys the complete ON, OW, and OV experience when being in the P.R.C. or Russia but a citizen from the P.R.C. being in the P.R.C. and a citizen from Russia being in Russia instead has the fully regulated access to the ON, OW, and OV, and enjoys the fully regulated experience in the ON, OW, and OV.
What kind of access to the ON, OW, and OV, and experience in the ON, OW, and OV a citizen from the P.R.C. or Russia has and enjoys when being in the U.S.A. or a member state of the E.U. is actually undecided, but we think for reaching harmony the cyber sovereignties of the U.S.A. and the member states of the E.U. are ruling in this case, though in theory the other possibility could be applied as well, specifically when a state infringes the paragraph CyS 1.1 or any other provision of the Articles of Association (AoA) and the Terms of Service (ToS) of the SOPR.
(ii) We do not respect double citizenship. Governing is the domicile or permanent residence, the place of taxability, as well as other determinants.
For example, a citizen of Russia remains a citizen of Russia even with a passport bought in Cyprus if not all determinats are fulfilled.
Comments and exemplary scenario to paragraph CyS.1.2:
(i) The paragraph CyS.1.2 provides a provision for a first SOPR member representing a government of a first state to take action against a violation of the paragraph CyS.1.1 by a second SOPR member representing a government of a second state.
(ii) An alternative formulation would have allowed that the Steering Committees of the SOPR take action against a violation of the paragraph CyS.1.1 by a SOPR member representing a government of a state. But eventually, this would have violated the CyS of said SOPR member and thereby also the paragraph CyS.1.1.
(iii) Only in the case of a violation of the paragraph CyS.1.1 the same access and experience that a first SOPR member of a first state has and enjoys when being in a foreign second state can be imposed on a second SOPR member of said second state when being a foreigner in said first state.
For example, a citizen from the P.R.C. or Russia has only a restricted access to the ON, OW, and OV and enjoys only a regulated experience in the ON, OW, and OV when being in the U.S.A. or a member state of the E.U., then a citizen from the U.S.A. or a member state of the E.U. can also have a restricted access to the ON, OW, and OV and enjoy a regulated experience in the ON, OW, and OV when being in the P.R.C. or Russia.
(iv) The paragraph CyS.1.2 can be altered by the Steering Committees of the SOPR for example if it is misused by a SOPR member representing a government of a state for making foregin politics.
Comments to paragraph CyS.1.3:
(i) Keep in mind that an ID space constitutes a hypergraph of one or more areas of authorization with related ranges of capabilities.
(ii) Eventually, the states remain the sovereigns within their real borders and the SOPR remains the sovereign in the ON, OW, and OV.
(iii) We highly recommend to not introduce any regulations respectively additional ID spaces because this causes significant disadvantages for example by binding enormous resources for managing an own national ID space, worsening or even blocking communication and collaboration, and generating huge costs.
Comments to general topics:
(i) Keep in mind that any alteration of a work of art, like for example the proposed CyS paragraphs, is only allowed by its creator in accordance with the international copyright law. This is also valid for the original and unique, iconic works of art titled
- Ontologic Net (ON),
- Ontologic Web (OW), and
- Ontologic uniVerse (OV),
and
both created by C.S., managed by the members of the Society for Ontological Performance and Reproduction (SOPR), and at least in the beginning legally secured and supervised by our business unit Ontonics.
(ii) Also, keep in mind that the contract between a member of the SOPR and the SOPR is valid for 5 years between the dates of year ending with 1 and 5 (1st of January xyz1 to 31st of December xyz5), and automatically extended if not decided otherwise by the SOPR many years before (e.g. 10 years announcement period).
(iii) All issues publicated in relation with the SOPR will be overworked, potentially summarized where needed, and publicated again together with the actual versions of the Articles of Association (AoA) and the Terms of Service (ToS) with the License Model (LM) of our SOPR.
Honestly, we like this third solution very much and hope the basic idea of this very harmonic because balancing solution is understandable. :)
05.March.2018
Ontonics Further steps
We have improved some projects and this time we are very sure that we reached the goal. Now, we have to research if another entity also got the same idea. Nevertheless, this could become a huge revolution in the related industrial sector.
In addition, we began to find out how to produce a basic element in a better and more cost efficient way.
06.March.2018
Ontonics Further steps
We continued the work on a basic technology by integrating the solution mentioned in the Further steps of the 24th of February 2018 that resulted in an interesting variant.
07.March.2018
iRaiment Further steps
We have designed a new feature watch model series.
We also have developed the next generation of the model 88 shown in the Further steps of the 17th of November 2016 by adding a new smartwatch model respectively wrist-worn Ontoscope model with a new design, a new model with a modular smartband, and also a new feature watch model. You will be amazed, mesmerized, fascinated, and much more.
08.March.2018
Comment of the Day
Electronic crown™
Elecrown™
Electrown™
e•crown™
Electronic couronne™
e-couronne™
e•couronne™
Couronne electronique™
Couronne-e™
Couronne•e™
Clarification
A sentence with X blockchain was nix, at least not for all kinds of application.
In fact, utilizing the blockchain technique for common applications, like for example
is not the best approach in most of the cases.
Indeed, the possibility exists that in some cases blockchain-based applications require only some few seconds and hence work up to 6 times faster than client-server applications, though we already question the competence of the genius (not really), who developed and implemented such an exemplary slow process of opening and closing a car with a mobile device requiring more than 10 seconds, but our related solutions based on the
work instantaneously, like for example the secure networking between a mobile device and a vehicle, and the one-time password technique.
Furthermore, everybody is talking about the next generation of mobile networking and its high performance, and in many cases there is even a direct access to the successor of the internet, our Ontologic Net (ON), over Local Area Network (LAN) and Wireless Local Area Network (WLAN).
Seconds? We do not know seconds. What is that?
Last but not least, the blockchain technique is definitely not a possibility to circumvent our Ontologic System (OS) and any related royalties, because it
In addition,
as we already discussed and showed in the past, and therefore our Society for Ontological Performance and Reproduction (SOPR) is at the spot either way.
Ontonics Further steps
We looked at a utilization of technology in a specific area since many years but only by a happenstance we created a more convincing realization today.
iRaiment Further steps
In the year 1842, Adrien Philippe invented the mechanism to wound and set a watch by the so-called couronne==crown, which replaced the key commonly used at that time. In the following years, this small innovation has become a part of daily life and today its significance for the human culture is unquestioned. Astonishingly, it took 172 years and the highly creative and visionary C.S. as well as our highly progressive corporation to change the status quo once again with our original and unique, iconic and crucial concepts, like for example our
(see for example the Ontonics Further steps of the 7th of July 2014 and iRaiment Further steps of the 12th of June 2016).
Today, we designed another new masterpiece of technology, which also features our original and unique creation of the e-Couronne™, for sure.
In this relation, we would like to make clear that adjusting the time of an electronic watch has absolutely nothing in common with the act of self-learning of a cognitive watch respectively a feature watch and smartwatch operated by our Ontologic System (OS) and a wrist-worn device based on our Ontoscope (Os).
Please keep in mind that our original and unique concepts are sufficiently creative, original and unique, revolutionary, crucial for a specific field, and directly connected with C.S. by representing characteristic expressions of the artist, and therefore are protected by the copyright and other rights of us, so that any description, any claim of invention, and any suggestion of having done our works by another entity also constitutes an infringement of our rights, because for example such an acting is merely an editing of our descriptions on the one hand and a misleading of the public about the true origin of our works and achievements on the other hand.
Patenting is not always required to protect a work of art.
Plagiarists will be sued and forced to inform the public in a correct and legal way.
12.March.2018
Comment of the Day
"LBD"
OntoLix and OntoLinux Further steps
We added to the section Mobile Device of the webpage Links to Hardware the link:
Besides the flexible polymer-based display technology of the concept of a roll-away computer, the input system based on keyboard, stylus or voice input, the ability of the display to change shape dynamically to accommodate the input system selected by the user, and the development of 3D functionality, we also find the exemplary application scenario of the mobile companion called Personal Navigation very interesting.
But we can also see the clear difference to our original and unique, iconic works of art titled Ontologic System and Ontoscope, both created by C.S.. For example, the input system provides different types of input mode and the Personal Navigation System (PNS) has rudimentary location and context sensitivity, but missing are the
- Augmented Reality (AR),
- Virtual Reality (VR), and
- Mixed Reality (MR),
(see also the Clarification of the 23rd of August 2017 for example) and also the aspects and features of
- self-reflection, self-image, or self-portrait, and also
- cybernetic reflection, augmentation, and extension,
(see the section History of the webpage Overview of the website of our Ontologic System (OS) OntoLinux and also the Comment of the Day of the 17th of October 2017)
Indeed, the DynaSheet was a fascinating vision at that time, though in some aspects we were already a step ahead with the Evolutionary operating system (Evoos) and The Proposal), but with our vision of the Ontologic System and the Ontoscope we were already far beyond this concept in the year 2006, and with others' mobile devices based on our works of art we even have past the envisioned state of technology in the last years.
14:06, 20:30, and 34:23 UTC+1
Mozilla DeepSpeech deep infringing
*** Work in progress ***
What a pity. From an online reference work we got the following informations: "Mozilla DeepSpeech is developing an open source Speech-To-Text [(STT)] engine based [on] Baidu's deep speech research paper. It is intended for end user usage in the coming months. [... referencing the document A TensorFlow implementation of Baidu's DeepSpeech architecture]".
The problem is that the Recurrent Neural Network (RNNs) and Deep Neural Network (DNN) frameworks, like for example PaddlePaddle of the company Baidu and TensorFlow of the company Google, are already based on a part of our original and unique, iconic work of art titled Ontologic System and created by C.S., specifically its OntoBot software component, therefore infringing our copyright or/and our other rights (see the Website review of the 2nd of February 2018), and the combination of PaddlePaddle, TensorFlow, or another DNN framework with speech recognition resulting in a STT engine like DeepSpeech or with a dialog system resulting in an Intelligent Personal Assistant (IPA) like Google Assistant of the company Google, Alexa of the company Amazon, Cortana of the company Microsoft, and Bixby of the company Samsung, and also to some extent Siri of the company Apple is, literally spoken, only deep infringing or deepening that copyright infringement, aka. illegal reproduction without proper licensing by our Society for Ontological Performance and Reproduction (SOPR).
(to be merged with the paragraph above)
composition of an essential part of our OntoBot software component with the related systems listed in the section Natural Language Processing of the webpage Links to Software of the website of OntoLinux in accordance with our original and unique overall integrating Ontologic System Architecture (OSA)
self-image brain of C.S. - see the last section of the last paragraph of the Investigations::Multimedia of the 18th of December 2009
For everybody, who still has not understood the situation, we simply repeat the subject matter in one sentence: With the works of art titled Evolutionary operating system (Evoos), Ontologic System, and Ontoscope C.S. created a cybernetic self-reflection, self-image, or self-portrait, augmentation, and extension, including a theory, technique, and technology, that should work like the own brain, but also like a (information) space, environment, world, or universe respectively reality, that we named Ontoverse (Ov) and New Reality (NR), and a worldview, belief system, and ontological spirit, and these unsupervised learning or deep learning frameworks are essential parts of said cognitive theory, technique, and technology, and also of said space, envrionment, world, or universe respectively our Ov and NR, and said spirit (for more details see for example the Clarification Caliber Special #1a of the 20th of May 2011, the Clarification Caliber Special #1b of the 21st of May 2011, the Clarification of the 16th of April 2016, the Clarification of the 18th of December 2016 and the Clarification #2 of the 13th of January 2017 once again).
We highly recommend
- reproduces our ontologic works in whole or in part on the one hand, because the internationally accepted copyright only allows that the licensing of the ontologic works is done by the artist C.S., and
- also includes voice-based assistants and smart speakers as well as In-Vehicle Infotainment (IVI) systems on the other hand,
which indeed addresses the actings of the Mozilla Foundation and its sponsors, the companies Canonical (Ubuntu) and Tata→Jaguar Land Rover once again, as well as other entities, and
whereby it should be doubtlessly clear that an Application Programming Interface (API) is only a set of subroutine or function definitions, protocols, and tools for building a software library or application, including the identifier or name of a
but not the software library or application.
We will not repeat that open source issue and our demand infinitely.
10:46, 16:09, and 17:57 UTC+1
Baidu already crossed the line
We are reading the Baidu document about Deep Speech 1, and also got some basic informations about Deep Speech 2 and 3, which all are based on our original an unique deep learning technique and basic approach called Learning by Doing here in the variant of learning by listening, as well as parallel processing on Graphics Processing Units (GPUs), so that we can already say that Deep Speech is also based on the same foundations introduced with our OS and used for Recurrent Neural Networks (RNNs) and Deep Neural Networks (DNNs) (see also the Clarification Caliber Special #1a of the 20th of May 2011 and the Clarification Caliber Special #1b of the 21st of May 2011). Bingo!!! Convicted!!!
And exactly
- generating,
- training, and
- applying
Artificial Neural Networks (ANNs) by utilizing for example
- metaprogramming,
- graph-based approaches, and
- model-based approaches
(see once again the Website review of the 2nd of February 2018) and
- the dialog system with its speech recognition, Automatic Speech Recognition (ASR), or Speech-To-Text (STT) component, and speech synthesis or Text-To-Speech (TTS) component, and
- other components
is one of the many original and unique features of our OS and its Ontologic System Architecture (OSA) directly connected with the artist C.S., and belonging to and representing the characteristic expression. It is not only about the fields of Artificial Intelligence (AI), Machine Learning (ML), Computer Vision (CV), Artificial Neural Network (ANN), and Multi-Agent System (MAS), dialogue management systems, and so on, which have been listed on separated webpages to emphasize this point, but the basic properties of the OS, the OSA, the Caliber/Calibre, and so on that integrates these fields, techniques, technologies, and systems on the basis of reflection, term rewriting, graph processing, RNNs, DNNs, Natrual Language Processing (NLP), Natural Image Processing (NIP), and so on.
Ontologic Web Further steps
We improved one of the platforms of our Ontologic Web (OW).
08:50, 09:51, 11:52, 14:09, and 45:09 UTC+1
SOPR #112
Some days ago, a white paper about a new cryptocurrency was publicated that claims to address the problems of complexity, user friendliness, and scalability of existing ordinary cryptocurrencies and distributed ledgers based on the blockchain technique.
But eventually, the cryptocurrency is merely based on the
All entities interested in our ontologic works have to take into account and observe the following facts at least:
- have been designed as Ontologic Applications and Ontologic Services (OAOS) more than 12 years ago,
- are based on our Ontologic System (OS) with its (mostly) validated and verified software components
and
- are managed and provided by our service platform OntoCoin and OntoTaler, and
- coordinated and consistend with the international monetary systems,
- compatible with the distributed ledgers and cryptocurrencies provided or/and supported by all leading companies in this field,
- integrated in the management and financial service platforms of our ON, OW, and OV, which already constitute the next net, web, universe, and reality, and
- managed by our Society for Ontological Performance and Reproduction (SOPR), which includes the "management of a financial transaction over one or more borders between ID spaces" (see issue SOPR #110 of the 3rd of March 2018).
- "blockchain-based systems in combination with Cyber-Physical Systems of the first generation (CPS 1.0) or the Internet of Things of the first generation (IoT 1.0),
- [...] blockchain-based (distributed computing) platform[s or distributed ledgers...], as well as
- cryptocurrencies
remain in the 5th ring and assigned ID spaces of the management structure of our ON, OW, and OV", which was a provision introduced exactly for those activities of external entities that correspond with our activities in this field on the one hand and we anticipated all the time on the other hand.
- exploiting our reputation and goodwill,
- mimicking our corporation, and
- misleading the public about the true origin of our works, in such a case of a partial copy.
In accordance with the Articles of Association (AoA) and the Terms of Service (ToS) with the License Model (LM) of our SOPR the following royalties will be due or are already due:
- value of regulated and currencies and any other legalized commodities in exchange for the tokens to be issued and
- the fees taken for the services done on the basis of this cryptocurrency or/and on one or more of the verified nodes of a site.
SOPR members enjoy a very low fee for a transaction within the ON, OW, and OV, if at all, and even some financial services for free, specifically on the basis of the SOPR's own digital currencies.
This raises the question if the SOPR should even prohibit any other digital currency (includes cryptocurrency) besides the SOPR's own digital currencies, as initially intended but not introduced to ensure neutrality. :)
No final decision has been made.
18.March.2018
SOPR #113
*** Proof-reading mode ***
We detailed the part of the Terms of Service (ToS) of our Society for Ontological Performance and Reproduction (SOPR) that is related to the digital currencies (e.g. cryptocurrencies) and financial applications and services of third entities, members of the SOPR, and the SOPR itself (see also issue #112 of the 16th of March 2018).
At first, we provide a concept formation and taxonomy for easier discussion:
- virtual (digital) currencies, "which are not issued by the state and lack the legal tender status declared by the government", and
- central bank digital currencies, digital fiat currencies, or digital base money.
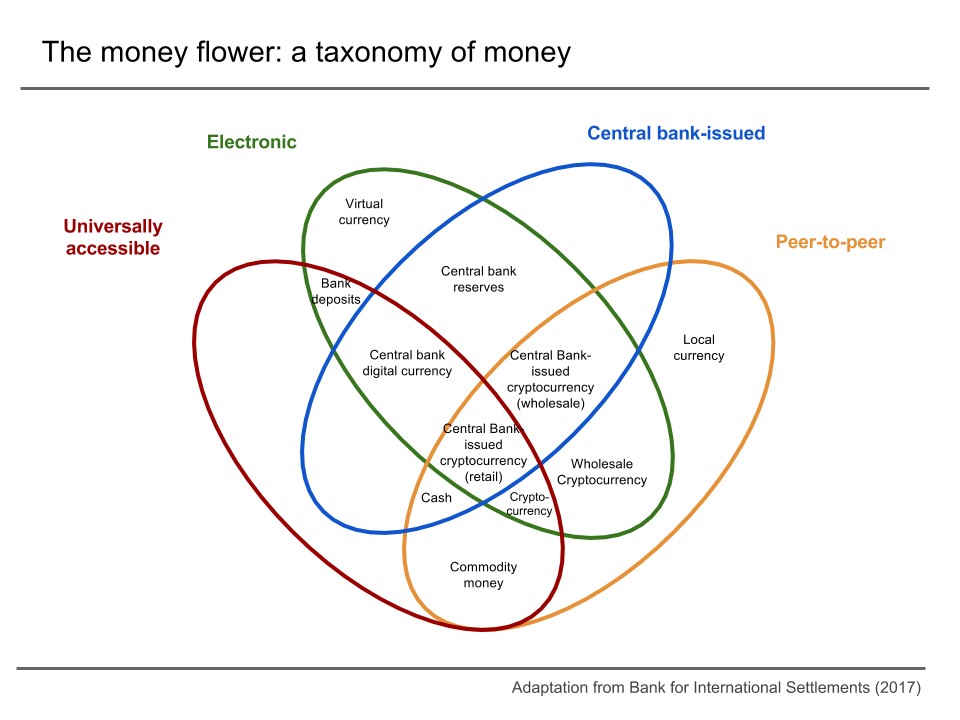

©© BY-SA 4.0 Stanjourdan
©© BY-SA 3.0 :( and OntomaX (references removed, Decentralized virtual currencies, Centralized cryptocurrencies, and Central bank cryptocurrencies added, scalled, screenshot made)
In addition, we already have as the
- on the one side the cultural, technological, and economical sovereignty of C.S.
- related to the creation of the iconic Ontologic System (OS) with its Ontologic Net (ON), Ontologic Web (OW), and Ontologic uniVerse (OV), and also the iconic Ontoscope (Os), and
- protected by international rights
and
- on the other side the cyber sovereignty of states,
- features of our OS, such as
- cybernetic self-reflection, self-image, or self-portrait of a user,
- every user gets an ID, that starts with onto#,
- personal World Wide Web-based infrastructure, network, and virtual drive, that supports the user centric migration, synchronization of applications and data, and communication, also known as cloud computing,
- user centric migration of applications and data from one computing machine to another, even from a personal computer to a cell phone, or an automotive media center,
- user account control enhancement, and
- IDentity and Access Management System (IDAMS) of our OS with verified state machines, and
- management structure of our ON, OW, and OV with its hypergraph-based rings and assigned ID spaces,
and
- regulations of the Articles of Association (AoA) of our SOPR that intertwine the legal and technical foundations in a harmonious way.
In the subsequent step, we utilize these concepts and taxonomy of digital currencies and these legal, technical, and organizational foundations to characterize and discuss the financial service platforms and digital currencies for our ON, OW, and OV.
Characteristic for our Ontologic Financial System (OFinS) is that it
- monetary system,
- banking system, and
- stock market or equity market,
- international monetary systems,
- national central banks, and
- local banks,
- provision of universal bank accounts,
- accepting deposits,
- making
- loans and
- investments,
- financial intermediary services,
- electronic asset transfer, specifically Electronic Funds Transfer (EFT),
- asset exchange, specifically currency exchange, and
- cashless payment services, as well as
- holding reserves equal to a fraction of the deposit liabilities,
- international monetary systems and
- national central banks,
but
- adjustments of key interest rates and
- backings of external
- financial institutions,
- physical currencies, and
- digital currencies,
- metacurrencies and
- digital private currencies,
- asset exchange meta system and
- Ontologic Payment System (OPS or OntoPay).
Characteristic for the Ontologic Currencies of our ON, OW, and OV is that they include various basic types:
- centralized or centrally managed digital currencies
- Ontologic Bank Digital Currency (OBDC) like digital fiat currency Central Bank Digital Currency (CBDC),
- decentralized managed virtual currencies
- reserve virtual currency OntoTaler,
- centralized cryptocurrencies
- Ontologic Bank CryptoCurrency (OBCC) like Central Bank CryptoCurrency (CBCC)
- wholesale and
- retail,
and
- Ontologic Bank CryptoCurrency (OBCC) like Central Bank CryptoCurrency (CBCC)
- decentralized cryptocurrencies
- reserve cryptocurrency OntoCoin,
- wholesale and
- retail,
- reserve cryptocurrency OntoCoin,
- asset basket determined digital and virtual currencies, and
- hybrids of these digital and virtual currencies,
as well as
Implication for handling activities of the SOPR itself
In the whole OS, including all rings and ID spaces, we have the
of the SOPR.
Implication for handling activities of members of the SOPR
In the 1st to 4th rings and assigned ID spaces the
are allowed only.
Implication for handling activities of distributed ledgers and digital currencies of third entities
In the 5th ring and assigned ID spaces the
are allowed in accordance with the regulation given in the Ontonics Further steps of the 20th of October 2017.
SOPR members solely using our OFinS avoid problems because for example a cryptocurrency token is property denominated in a real currency:
- stored-value money card (e.g. gift card or telephone calling card), debit card, or credit card,
- online payment system, or
- conduit of exchange,
This also results in a value creation for the SOPR members due to the value of a more seamless process.
Exemplary business processes:
- OntoCoin and OntoTaler,
- OntoPay,
- Electronic Commerce Modeling Language (ECML) provided by a SOPR member (e.g. Microsoft, IBM, etc.), and
- payment system or/and digital wallet provided by a SOPR member (e.g. and Google Pay, Apple Pay, Microsoft Pay, Samsung Pay, etc.),
- Electronic Commerce Modeling Language (ECML) provided by a potential SOPR member
- payment system or/and digital wallet provided by a potential SOPR member (PayPal, Visa Checkout, Mastercard, etc.)
19.March.2018
Investigations::Multimedia, AI and KM
*** Work in progress - update in accordance with epilog and OS property of proof-carrying ***
"We're a Fintech Company With a Social Cause [And we show what social cause means in this relation.]",
"BanQu is a software technology company on a mission to connect refugees, the displaced, and the world's poorest to the global economy through a secure, portable digital identity that maintains transaction history through a proprietary blockchain-based platform. [See the Feature-List #2 for the note "every user gets an ID, that starts with onto#" in connection with the World Wide Web, and our Ontologic Net (ON), Ontologic Web (OW), and Ontologic uniVerse (OntoVerse or OV).] ",
"[...] banks or other formal financial institutions [...]" [We do not know what a formal institution is but we know that using the term formal in this context constitutes a speech act stealing. See the sections Formal Modeling and Formal Verification of the webpage Links to Software of the website of OntoLinux. This cheap trick is applied on its whole website.]",
"[...] verifiable identity [...] [See the section Basic Properties of the webpage Overview for the OS property of (mostly) being validated and verified, and once again the Feature-List #2 for the note "every user gets an ID".]",
"[...] we believe [...] We'd love [...] [As we said before, such cheap tricks are applied on its whole website.]",
"[The company] has developed and deployed the first blockchain-as-a-service software platform [...] [Here we have a functionality provided as a Service (aaS), which is related to e.g. the cloud computing paradigm.]",
"The Company's "Economic Identity Passport" is a revolutionary change for corporations, governments and [International Non-Governmental Organizations (]INGOs[)] looking to become proactive in meeting their [Sustainable Development Goals (]SDGs[)] commitments by 2030. [See the webpage Ontologic Applications and all comments made to quotes related to identity.]",
"[The company] is using distributed ledger technology directly for the benefit of the most vulnerable in this world while driving purpose and profit for its investors and partners. [So much about its social cause.]",
"Software architect with deep experience building highly-scalable cloud-based technology platforms. [The functionality provided as a Service (aaS) already pointed to the field of cloud computing. See the section Network Technology of the webpage Links to Software of the website of OntoLinux.]",
"He currently serves as Chairman of the Wall Street Blockchain Alliance, a non-profit trade advocacy group whose mission is to guide and promote comprehensive adoption of blockchain technology across financial markets. He also serves as Chief Executive Officer of [...] a financial technology and strategic advisory firm. Prior to this, Ron served as CEO of [...] a pioneering software and communications provider of secure transaction and information platforms for financial market participants. Before this he held a variety of senior roles at Thomson Reuters, the global news and information firm, culminating as Global Head of Trading Analytics. [... She] is [Executive Vice President (]EVP[)] and [Chief Executive Officer (]CEO[)] of [... a s]ubsidiary at [American International Group (]AIG[)]. She is a Member of the Board of Directors of Credit Suisse Group AG and Credit Suisse AG as well as a Member of the Audit Committee. [...] Previously, [she] was President and CEO of [Europe, the Middle East and Africa (]EMEA[)] for AIG and led the insurance business in Europe, the Middle East and Africa. [She] was a founding partner and financial analyst for NZB NeueZuercher Bank in Switzerland. [Is not it curious somehow, that such people belong to a start-up that has such a social cause? As in the case with its way of marketing and mimicking, its social cause, and the benefit, purpose, and profit for its investors and partners, we have the impression that somebody is confusing altruism and philanthropism with capitalism.]",
"Cashless World 2016 Award Winner [...] Digital Banking category winner [At this point, it should be clear what kind of company we are talking about and it should also become clear what is its true business goal.]",
"[...] verified identity [...] [See the other comments made to quotes related to the subject of identity.]",
"[Its Chief Executive Officer (CEO)] Named to Wall Street Blockchain Alliance [(WSBA)] Economic Inclusion Working Committee [Literally spoken, we only see business as usual.]",
"Economic Identity is the marriage of identity and commerce, resulting in a global, vetted, and manageable asset. This identity consists of the digital or electronic credentials that define a person's history of economic interactions in the world economy. [See once again the section Basic Properties of the webpage Overview for the OS property of (mostly) being validated and verified and the Feature-List #2 for the note "every user gets and ID", and also the AutoSemantic extension package for the list point "e-commerce ready", that are integrated by the Ontologic System Architecture (OSA), while keeping in mind that a driver is a user of our OS in this context. In addition, we also have the OntoLogger software component, which is based on the so-called lifelog, which again is a detailed chronicle of a person's life respectively a quantified self-image (selfie but in a more general sense than a picture), which again also comprises the record of a person's history of economic interactions.]",
"Since 60% of the 2.7 billion unbanked people already own mobile phones, these devices make the best platform for these people to connect to the global economy. [Mobile phones and smartphones are included in our iconic Ontoscope. This classification will become relevant in relation with a comment made to a quote also related to mobile phones.]",
"As they start accumulating a transaction history on the BanQu blockchain, the unbanked also develop a tractable, vetted financial and personal history. Our blockchain platform allows people to record a variety of transactions including remote purchases, funded wallets, term purchases, cash disbursements, property records, health records, education records, and credit histories among others. [See the section Human Simulation/Holomer of the webpage Links to Software and once again our OntoLogger, specifically the HOLOgraphic MEdical Record (HOLOMER) and the learning envrionment Salt and Pepper (Salt 'n' Pepper or S&P) referenced therein, the comment made to a quote about economic identity above, and the comment made to a quote about mashup of selfie below.]",
"[...] capabilities to assist [...] [In this context, this is another speech act stealing. See the section Exotic Operating System of the webpage Links to Software and the OntoBot software component.]",
"[...] components [...] [In this context, this is another speech act stealing. See the webpage Components.]",
"[The company] allows the unbanked to set up a personal digital identification profile [...]. [See once again the Feature-List #2 for the note "every user gets and ID".]",
"[The company] has developed the first ever blockchain economic identity technology solution that enables a secure and immutable platform for creating economic opportunities for people around the world who are refugees and/or living in extreme poverty. [From the legal point of view it does not matter at all who the people around the world are, because the company also offers the solution and related services to financial institutions and companies. But from the social point of view it does matter, though in a totally different relation, because the refugees and/or people living in extreme poverty are used as part of its marketing story for selling the solution and services to financial institutions and companies to increase the benefit and driving the purpose and the profit of its shareholders. We would also like to give the recommendation to take a look at the Peer-to-Peer Virtual Machine (P2PVM) Askemos, which is also based to a large extent on our Evolutionary operating system (Evoos) described in The Proposal and listed in the section Exotic Operating System of the webpage Links to Software, and the related OntoLix and OntoLinux Further steps of the 13th of October 2017.]",
"The [...] platform uses a proprietary (patent pending) method to create a mashup of selfie plus other key human characteristics for people with no access to technology or banking. [Ah, what ...? Why does the company attempt to patent the method at all, when it is utilized for such a social cause? Where is the logic for pretending that another entity utilizes our Intellectual Properties (IPs)? Furthermore, a mashup is a Web 2.0 page or application, and the Feature-List #1 includes the list point "[i]ntegration of Web 2.0 content like maps[, blogs, wikis, or mashups]". In addition, see once again the section Human Simulation/Holomer of the webpage Links to Software to find all human characteristics. Moreover, by utilizing self-images (selfies in the sense of a picture) plus other key human characteristics in addition to a lifelog the creation of a self-reflection, self-image, or self-portrait has been copied one more time but in a different way than it did with the lifelog. Self-reflection, self-image, or self-portrait on the one hand is listed in the section History of the webpage Overview and on the webpage of our Caliber/Calibre and on the other hand is an essential element of the original and unique, characteristic artistic expression represented with our OS created by C.S.. In combination with all the other features and evidences shown in this investigation the company crossed the white, yellow, or red line in this way and eventually infringed our copyright.]",
"Our technology provides a platform where [people] can maintain a free, secure online profile that provides them with a universal fiscal ID and allows them to begin tracking their relationships and transactions. [See once again the Feature-List #2 for the note "every user gets an ID" in the context of the World Wide Web and our Ontologic uniVerse (OntoVerse or OV). Also note the utilization of the terms relationship and transaction taken from the webpage of the Ontologic File System (OntoFS) software component of the website of OntoLinux.]",
"What is Blockchain? In simple terms, it is a new type of data application or ledger, storing immutable data, which can be directly shared, without requiring a central administrator. This contrasts with traditional databases, which have one single administrator that owns and controls the data. [] Also, blockchain transactions are based on cryptography which makes them inherently more secure than any traditional database or system today. [Obviously, they have never heard about the field of Content-Addressable Storage (CAS), so we recommend to learn a little and read the OntoLix and OntoLinux Website update of the 2nd of May 2016 and 1st of February 2018, and the last section of the OntoLix and OntoLinux Further steps of the 21st of January 2018, and also as a complement the OntoLix and OntoLinux Website update of the 13th of February 2018.]",
"Universal Design [In this context, this is another speech act stealing. See the Ontologic uniVerse (OntoVerse or OV) once again.]",
"Unlimited Use Cases [At this point, it has become clear that it is indeed a common start-up that has jumped on the bandwagon of our OS.]",
"Supports any language. [This means the platform is multilingual.]",
"Economic Identity [] Creates your global economic identity allowing you to transact with anyone on the planet. [See once again the Feature-List #2 for the note "every user gets an ID" in the context of the World Wide Web and our Ontologic uniVerse (OntoVerse or OV).]",
"Immutable human-characteristics based (selfie) ID owned by the user who creates it. [As we said in a comment made to a related quote above, this explicit description of the immutable human-characteristics based (selfie) ID provides the required causal link with the original and unique work of art titled Ontologic System and created by C.S. and therefore is an evidence for a copyright infringement. Below we come back to this important observation.]",
"[...] universal ID [...] [See the other comments made to related quotes above that include secure, portable digital identity, verifiable identity, verified identity, immutable human-characteristics based (selfie) identity, and economic identity. Here we have it directly connected with the Ontologic uniVerse (OntoVerse or OV) and the section Singularity Ontoverse of the webpage Caliber/Calibre, and in the overall view another evidence for the copyright infringement. In this relation, it does not matter that we use a network of telescopes and capability-based approaches, and on top of them blockchain-based approaches, because a significant part of the characteristic expression of the OS is this connection, or better said, fusion of real and virtual identities of an owner.]",
"[The company] lowers the cost of identity management systems for various government agencies [...]",
"Financial institutions can use our platform to augment and automate compliance with "know your customer" (KYC), "anti-money laundering" (AML) and other identity authentication requirements under applicable banking regulations. We aim to support the financial sector as an approved technology vendor, verifying the identities of customers they serve. [Honestly, we think that this service is the true main activity of the business. Furthermore, augmenting and automating are two essential characteristic functions of our OS as well. Using these two terms is the next speech act stealing to confuse the public.]",
"Contact us to learn how your bank or financial services company can benefit from working with the BanQu platform. [But also contact us to learn that there are legal issues.]",
"Everywhere There is a Phone, There is Identity [Here we have once again the already mentioned part of the original and unqiue, characteristic expression of the ontologic works of C.S. represented by the connection between the secure, portable, digital, verifiable, verified, immutable, and human-characteristics based (selfie), universal, economic identity of our OS with our Ontoscope, which provides us the next evidence for the copyright infringement.]",
"Why should banks and the few decide how economic resources are pooled and shared to transact? The short answer is; they shouldn't. [Ah, what ...? We have the Executive Vice President (EVP) and Chief Executive Officer (CEO) of a subsidiary of American International Group (AIG), and member of the board of directors of Credit Suisse Group AG and Credit Suisse AG in the management team of this company, and it really wants to sell us this attitude? The short answer is: Computer says No, which means we shouldn't buy that nonsense.]",
"As the BanQu Network expands over the coming quarters and years, it is important to remember that our goal is singular and singular alone; to end world poverty by 2030. [See the webapge Introduction of the website of OntoLinux for the reference to a singularity and once again the section Singularity Ontoverse of the webpage Caliber/Calibre.]",
"What distributed ledger network does BanQu run on? contracts. Ethereum is the actual blockchain and 'ether' is the currency. Ethereum allows for more flexibility with developing blockchain applications, including storing additional data and not just strict financial transactions. [We already discussed the distributed ledger Ethereum with its Peer-to-Peer Virtual Machine (P2PVM) even in relation with IDentity and Access Management Systems (IDAMSs) in the Clarification of the 17th of October 2017 and also in the context of a more general view in the OntoLix and OntoLinux Further steps of the 5th of July 2017.]",
"BanQu's patent-pending technology enables storage of key identity data directly on the blockchain without compromising scale and response times. [With the information found on its website we are not sure what the company has truly invented.]",
"Why is blockchain better and more sustainable? It's more secure than a traditional database because it uses a public key infrastructure (PKI), where users get two keys that don't perform the same function - one for encryption and one for decryption. [We only quoted this for the fun of experts in the fields of databases management systems and file systems.]",
"What is a smart contract and how are people using it? Smart contracts are essentially tiny computer programs that can live on the blockchain. These programs get stored, verified, and executed all by the same blockchain network. This allows for more advanced functions to take place on the blockchain such as verifying an individual meets certain criteria or allowing for the self-regulating of funds or food aid distributed by various organizations. [First of all, a smart contract is defined as a computerized transaction protocol that executes the terms of a contract in a runtime environment. But more important is that we discussed exactly this connection of verification with blockchain-based systems in relation with Ethereum and similar distributed ledgers, that are based on the techniques of the smart contract protocol and the blockchain, and already considered the combination of a verified smart contract with a distributed ledger as a legal issue if not to say a copyright infringement (see once again the OntoLix and OntoLinux Further steps of the 5th of July 2017 and the Clarification of the 17th of October 2017, and also the OntoLix and OntoLinux Further steps of the 13th of October 2017 once again, and the Ontonics Further steps and Investigations::Multimedia of the 20th of October 2017).]",
"[The company] provides a range of services to NGOs, financial institutions, and companies. They can all be put into the larger category of economic identity services. Verifiable economic identities are the backbone of all financial transactions. In the U.S., identity is verified through a social security number or driver's license. [Now guess why we have added in the Feature-List #2 the note "every user gets an ID, that starts with onto#" already in the year 2008. Exactly for this reasons, which is directly connected with our Ontologic uniVerse (OV), Ontologic Financial System (OFinS), and many other applications.]",
"[... the company] provides a neutral method for verifying identity and enabling participation in the global economy. [See once again the webpage Introduction of the website of OntoLinux to find out that the company is mimicking C.S. and our corporation indeed.]", and
"Chemonics [How cheap is that to confuse the public in relation with our business technology office Ontonics in this way?]".
This is also a case where the verdict was not easy to made.
Indeed, we have the combination or integration of several identical terms, techniques, and technologies. But the secure, portable, digital, verifiable, verified, universal, economic, and human-characteristics based (selfie), as well as proof-carrying identity created by making a partial lifelog, digital chronicle, or journal of a person's life, which is
- represented as an "online profile" respectively a "mashup of selfie plus other key human characteristics[, ...] relationships and ["a variety of"] transactions", and
- realized as an application running on a mobile phone
might not be sufficient to claim for a copyright protection, or to show a causal link and prove a copyright infringement due to exceptions from such a protection such as for example an act of fair use, a Scène à faire, and an ordinary technological progress.
But the required causal link is given with the conjunction of
- this specific way of creating a virtual identity that reflects the real identity and
- the statements "60% of the 2.7 billion unbanked people already own mobile phones" and "everywhere there is a phone, there is identity",
that has to be understood in the sense that the mobile phone with the virtual identity of a user constitutes a cybernetic self-reflection, self-image, or self-portrait, augmentation, and extension of the real identity of the user. The later is an original and unique, characteristic expression of the works of art titled Ontologic System and Ontoscope, and created by C.S..
This understanding is further emphasized by the facts that
- these ontologic works belong together, as can be seen easily by the points that the Ontoscope is
- included in the Ontologic System as well when viewed from the very general point of view, and also
- operated by the Ontologic System,
and
- the partial lifelog or quantified self enables the owner to become qualified and active, and in this way the quantified self becomes the qualified self, which differs from the original lifelog paradigm and therefore provides another causal link, because this augmentation and extension of the lifelog paradigm and the resulting qualified self is also an original and unique, characteristic expression of the works of art titled Ontologic System and Ontoscope, and created by C.S..
(see also the Clarification of the 14th of December 2016 and the Clarification #2 of the 13th of January 2017).
Honestly, our impression is that the company has attacked exactly this aspect of our ontologic works after we discussed it to create a legal loophole or clear the way, as we have observed it with activities related to the foundational distributed ledger,
so that the whole endeavour looks like a common start-up camouflaged by preventing a social cause, which is emphasized with for example the description of its platform and our technology.
We highly recommend that the company with its partial plagiarism and island system becomes a member of our SOPR or simply think about stopping its operation.
The same holds for all financial institutes, who failed with their blockchain-based systems due to the same or other reasons. We already have our Ontologic Financial System (OFinS) (see the issue #113 of the 18th of March 2018 (yesterday)).
21.March.2018
Clarification
We have to kill a myth. But at first we would like to give some descriptions or definitions about the relevant fields:
"A Turing machine is a mathematical model of computation that defines an abstract machine, which manipulates symbols on a strip of tape according to a table of rules." It is used for theoretical discussion, specifically "to prove properties" [and "fundamental limitations on the power of mechanical"] computation in general and in particular, [such as] the uncomputability of the Entscheidungsproblem ("decision problem")", but does not make any statement about practicability of a real computing system.
"[A] virtual machine (VM) is an emulation of a computer system. Virtual machines are based on computer architectures and provide functionality of a physical computer.
There are different kinds of virtual machines, each with different functions:
- System virtual machines (also termed full virtualization VMs) provide a substitute for a real machine. They provide functionality needed to execute entire operating systems. A hypervisor uses native execution to share and manage hardware, allowing for multiple environments which are isolated from one another, yet exist on the same physical machine. [...]
- Process virtual machines are designed to execute computer programs in a platform-independent environment.
Some virtual machines [...] are designed to also emulate different architectures and allow execution of software applications and operating systems written for another CPU or architecture. Operating-system-level virtualization allows the resources of a computer to be partitioned via the kernel's support for multiple isolated user space instances, which are usually called containers and may look and feel like real machines to the end users."
"In operating-system-level virtualization, a physical server is virtualized at the operating system level, enabling multiple isolated and secure virtualized servers to run on a single physical server. The "guest" operating system environments share the same running instance of the operating system as the host system. Thus, the same operating system kernel is also used to implement the "guest" environments, and applications running in a given "guest" environment view it as a stand-alone system."
"An operating system (OS) is system software that manages computer hardware and software resources and provides common services for computer programs[, also known as applications].
Time-sharing operating systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation of processor time, mass storage, printing, and other resources.
For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware [...]".
"Decentralized computing is the allocation of resources, both hardware and software, to each individual workstation, or office location. In contrast, centralized computing exists when the majority of functions are carried out, or obtained from a remote centralized location."
"Based on a "grid model" a peer-to-peer system, or P2P system, is a collection of applications run on several local computers, which connect remotely to each other to complete a function or a task. There is no main operating system to which satellite systems are subordinated."
Systems
- P2P computing
- file sharing
"Distributed computing is a field of computer science that studies distributed systems. A distributed system is a model in which components located on networked computers communicate and coordinate their actions by passing messages. The components interact with each other in order to achieve a common goal. Three significant characteristics of distributed systems are: concurrency of components,
Architectures
- client-server
- n-tier
- Peer-to-Peer (P2P)
- grid computing
- cloud computing
"A distributed operating system is a software over a collection of independent, networked, communicating, and physically separate computational nodes. They handle jobs which are serviced by multiple CPUs. Each individual node holds a specific software subset of the global aggregate operating system. Each subset is a composite of two distinct service provisioners. The first is a ubiquitous minimal kernel, or microkernel, that directly controls that node's hardware. Second is a higher-level collection of system management components that coordinate the node's individual and collaborative activities. These components abstract microkernel functions and support user applications.
The microkernel and the management components collection work together. They support the system's goal of integrating multiple resources and processing functionality into an efficient and stable system."
"A distributed ledger [...] is a consensus of replicated, shared, and synchronized digital data [...]. There is no central administrator or centralized data storage.
A peer-to-peer network is required as well as consensus algorithms to ensure replication across nodes is undertaken. One form of distributed ledger design is the blockchain[-based] system [...].
The meaning of the word "blockchain" remains controversial. While some people state it is synonimous with a Distributed Ledger [...], others argue that technically it would only apply to linear blockchains [...] and not to Directed Acyclic Graphs [(DAGs) ...]. Therefore according to the latter definition, not all distributed ledgers have to necessarily employ a chain of blocks to successfully provide secure and valid achievement of distributed consensus: a blockchain is only one type of data structure considered to be a distributed ledger.
Distributed Ledgers are mostly known because of their use as cryptocurrencies, even if technically speaking the cryptocurrency and the underlying ledger are two different things. [...]
Other possible uses beside cryptocurrencies include Smart Contracts
"Ethereum is an open-source, public, blockchain-based distributed computing platform [respectively distributed ledger]
"Ether is a cryptocurrency whose blockchain is generated by the Ethereum platform."
"Ether is a fundamental cryptocurrency for operation of Ethereum, which thereby provides a public distributed ledger for transactions."
"Ethereum provides a decentralized Turing-complete virtual machine, the Ethereum Virtual Machine (EVM), which can execute scripts using an international network of public nodes.
The Ethereum Virtual Machine (EVM) is the runtime environment for smart contracts in Ethereum. It is a 256-bit register [virtual] stack [machine ...]. It is the fundamental consensus mechanism for Ethereum. It is sandboxed and also completely isolated from the network, filesystem or other processes of the host computer system. Every Ethereum node in the network runs an EVM implementation and executes the same instructions."
In the Ethereum platform "[s]mart contracts are high-level programming abstractions that are compiled down to EVM bytecode and deployed to the Ethereum blockchain for execution."
"Executing code within the Ethereum network takes time, and execution is generally pretty slow compared to other VMs. For every instruction, there's a cost associated, and an internal counter keeps track of the total cost, which is charged to the user. When a user initiates an execution through a transaction, they reserve some cash, which is the maximum amount they're willing to pay."
We consider verified smart contracts as Ontologic Applications (OA) (see also the Ontonics Further steps of the 20th of October 2017).
In accordance with the common sense about the definitions and descriptions of the foundational fields the Ethereum platform and its Ethereum Virtual Machine are
The P2PVM Askemos, blockchain platforms Ethereum, Iota, and others with or without VM, smart contract transaction protocol, Directed Acyclic Graph (DAG), and so on are relatively old, retrograde, and in some specific aspects even outdated technologies (see the Clarification of the 16th of October 2017 but also the OntoLix and OntoLinux Further steps of the 26th of October 2017).
When we designed our OS we were aware about such systems like Askemos, for sure, but they did not convince us and therefore we developed something new, original and unique. The successor is included in our iconic Ontologic System (OS) with the OntoCore, OntoBot, and OntoLedger software components. In comparison with these older systems our OS is at least the next generation, but in the general view we think it is 2 or more generations ahead (see the OntoLix and OntoLinux Further steps of the 13th of October 2017 and the Clarification of the 17th of October 2017). Distributed ledgers in all flavours are merely a specific functionality in our OS (see the OntoLix and OntoLinux Further steps of the 18th of October 2017 and once again the Ontonics Further steps of the 20th of October 2017).
Honestly, we do not know who the clever gal or guy was that came up with such a totally ridiculous nonsense and even started to promote the Ethereum Virtual Machine as an operating system or a defining element of the Web 3.0.
Also, we are not in the mood to explain the facts every month again and again.
Furthermore, we have to give the reminder that claiming wrong facts to mislead the public for gaining an economic advantage as a company is an illegal act of unfair business practice.
Ontonics Further steps
We developed the next generation of a device and are surprised once again now that we were able to improve this technology and also how we did it.
24.March.2018
Investigations::Multimedia, AI and KM
*** Proof-reading mode - comparison with case of 19th of March 2018 ***
In addition, we also made clear that this special Known Traveller Digital Identity (KTDI) system is basically very similar to or even the same system like the Economical IDentity (EcoID) system discussed in the Investigations::Multimedia, AI and KM of the 19th of March 2018 and therefore suffers from the same legal issues.
In a subsequent step we worked through a foundational report written by the World Economic Forum, the company Accenture, and the members of the Future of Security in Travel Working Group that includes the following informations:
"[...] collaborative relationships [...] [We note directly at the start the first example of a speech act stealing. This cheap trick is applied in its whole report.]",
"Emerging technologies - from biometrics to distributed ledger to machine learning [...] [We note the terms distributed ledger (see for example the Clarification of the 21st of March 2018) and Machine Learning (ML) (see the section Softbionics (SB) of the webpage Terms of the 21st Century of the website of OntoLinux).]",
"Throughout 2017, the Shaping the Future of Security in Travel project convened stakeholders in multiple day-long workshops and working calls on the topic of digital identity to continue to shift security in travel forward. This report details the Known Traveller Digital Identity concept as a catalytic prototype capable of transforming the travel and tourism sector as well as medical services, education and beyond. [As in the case of the EcoID system (see once again the Investigations::Multimedia, AI and KM of the 19th of March 2018) it is intended to utilize the system in a general way, which has to be interpreted as another unsuccessful attempt to create a legal loophole with a similar or the same type of system for circumventing our Ontologic System (OS). We also have observed this attempt with IDAMSs of some other collaborations of industrial companies.]",
"Together with its partners, the World Economic Forum explored solutions to seamless and secure travel challenges and developed the Known Digital Traveller Identity concept as part of its project, Shaping the Future of Security in Travel. [All these quotes and comments made by us in this investigation show that the concept behind the KTDI system has not been developed by those entities, even not this specific field of application respectively Ontologic Application (OA) because technologies like the ones mentioned in the sections Teleportation 1 Stellar and Teleportation 2 Interstellar have to be considered as ways of travelling, too.]",
"Fourth Industrial Revolution technologies such as biometrics, blockchain, cryptography and mobile devices enable efforts to overcome challenges [...] [We note the terms Fourth Industrial Revolution, also designated as Industry 4.0, and mobile device, as well as the facts that on the one hand the blockchain technique is a little older and hence does not belong to the initial description of the field of the Industry 4.0 at all, and on the other hand the Fourth Industrial Revolution or Industry 4.0 is one of our many achievements based on the creativity and visionary abilities of C.S. doubtlessly proven with the iconic works of art titled Ontologic System and Ontoscope, that are the foundations for the fields of Cyber-Physical Systems of the second generation (CPS 2.0), Internet of Things of the second generation (IoT 2.0), and Networked Embedded Systems of the second generation (NES 2.0) (see for example the Clarification of the 12th of October 2017 and the many other related messages of the year 2017 (keywords Cyber-Physical Systems, CPS, Internet of Things, IoT, Networked Embedded Systems, NES, and of course Industry 4.0), and also the Ontonics Further steps of the 20th of October 2017 related to both, the fields of CPS, IoT, and NES, and also distributed ledgers.]",
"This Known Traveller Digital Identity concept is founded on the principle that an individual traveller has control over the use of their own identity and its components. [In comments made to quotes below the issue being document in this investigation becomes more clear. Besides this, see the webpage Components of our original and unique, iconic OS.]",
"Access to verified personal biometric, biographic and historical travel data will enable entities along the way to undertake advanced risk assessment, verify travellers' identities and provide seamless access through biometric recognition technology. [See the section Basic Properties of the webpage Overview for the OS property of (mostly) being validated and verified, the note "every user gets an ID, that starts with onto#" in the Feature-List #2 of our OS, and once again the case of the Investigations::Multimedia, AI and KM of the 19th of March 2018.]",
"As presented in the 2017 report on Digital Borders: Enabling a secure, seamless and personalized journey, incorporating new technologies into the process will dramatically reshape how the industry and governments manage the secure cross-border movement of people. To do this, a cohesive vision for the future of security in travel must include user-centricity, digitization and trustful cooperation. [Keep in mind that we also have cross-border movement of people in our Ontologic Net (ON), Ontologic Web (OW), and Ontologic uniVerse (OV). We also see here that our OntoLab, The Lab of Visions, is mimicked to exploit our reputation and goodwill, which is one of the main reasons for such activities. Furthermore, in relation with the user-centricity see the Investigations::Multimedia of the 14th of January 2018 (keyword homocentricism).]",
"[...] future vision [...] [This is just another example for the exploitation of our reputation and goodwill in relation with our OntoLab, as also mentioned in the comment made to the quote before.]",
"Digital Identity as a lever for change [As a matter of fact, this change based on an identity, which is the fusion of the real or physical identity and the virtual or digital identity of an owner, is one of the characteristic expression represented with the original and unique work of art titled Ontologic System and created by C.S..]",
"1. Distributed ledger enables trust in the network without the control of one central authority [] 2. Cryptography allows an appropriate level of security in authorization and sharing of information [] 3. Biometrics connect the physical and digital world and ensure the legitimate use of identity information [] 4. Mobile interfaces and devices allow travellers to carry their digital identity with them and to choose to share it accordingly [With the exception of explicitly using the terms distributed ledger and consensus algorithm (see the related OntoLix and OntoLinux Further steps of the 5th of July 2017 and once again the Clarification of the 21st of March 2018) the other 3 points are provided by our OS as well. In addition, we note that biometrics references the aspects and features of cybernetics, specifically cybernetic self-reflection, self-image, or self-portrait, and augmentation, and extension (see also the section History of the webpage Overview and the webpage of our Caliber/Calibre). Specifically the combination of the statements "[b]iometrics connect the physical and digital world" and "[m]obile interfaces and devices allow [owners or users] to carry their digital identity", which is connected with their physical identity by biometrics is important to note, because by adding more features the white, yellow, or red line is crossed in relation with an infringement of our rights.]",
"In addition, the growing adoption and use by state and non-state entities of electronic passports (ePassports) could provide the means to unlock new ways to facilitate the low-risk traveller's journey, while still ensuring high levels of security. [But we could not find such a means in the report, specifically the connection or even integration of the biometric passport, which is the correct designation for the electronic passport, with the distributed ledger technology. See also the comment made to a related quote below.]",
"As expected with emerging technologies, sufficient evidence to identify the one "best" solution does not yet exist. Every technological decision taken in designing such an innovative concept must be considered in terms of its anticipated advantages and disadvantages. [Obviously, this statement is nonsense, because the best solution is our OS, as it is proven with this partial plagiarism once again. The few details of implementation does not change this fact.]",
"[...] three key values [...] [This is a reference to the 3³ Theme of C.S..]",
"[...] the traveller must be given the opportunity to move from playing a passive role to one of active partnership in the security process. By self-selecting the sharing of their digital identity, travellers will be integral to the security process and experience the reward of a more personalized and seamless journey. [With this statement we already get an important evidence for the copyright infringement that is the change from a passive to an active role by the secure, portable, digital, verifiable, verified, universal, economic, and human-characteristics based (selfie), as well as proof-carrying identity, or said in our words by creating a cybernetic self-reflection, self-image, or self-portrait, and augmentation, and extension, as well as a qualified self. See the section Basic Properties of the webpage Overview for the OS properties of (mostly) being validated and verified, and proof-carrying, and also note that proof-carrying is a mechanism, which allows a control system or host system to verify properties about a subject via a formal proof that accompanies the subject's property of interest. The control system or host system can quickly verify the validity of the proof and compare the conclusions of the proof to its own security policy to determine whether the subject is safe to handle. For sure, this mechanism applies for the quantified self, qualified self, and cybernetic self-image and extension of a user and a user's identity, such as onto#, as well.]",
"Recommendations [Another speech act stealing. See the webpage Ontologic Applications.]",
"The Known Traveller Digital Identity concept is the first step towards achieving this systemic shift in travel security. [This is a lie because our OS came first and seems to be first.]",
"[...] our shared vision for the future of [...] [This is once again the speech act stealing related to vision.]",
"Stakeholders should articulate sustainable and trusted business models for delivering Known Traveller Digital Identity capabilities and infrastructure. [Besides the aspects of sustainability and trust, as well as the term models, we also have the terms capabilities and infrastructure, which leads us once again to the basic properties of OS and its components, such as the capability-based OntoCore.]",
"[...] cybersecurity [...] [Indeed, we revived the fields of cybernetics and cyberspace with our safe and secure OS.]",
"The concept presented in this report proposes using available Fourth Industrial Revolution technologies to demonstrate the ability to re-engineer the border-crossing experience. [We note the term experience which is also used in the field of Mediated Reality (MedR), specifically in its subfield of Virtual Reality (VR). In relation with the term digital border we already had the impression that concepts of the virtual or digital reality are transformed into the initial or physical reality, which is emphasized with the term border-crossing experience. Nevertheless, our OS comprises both, reality and virtuality, as can be seen easily with the list points of the section Basic Properties of the webpage Overview that are related to various realities.]",
"Lack of integration between physical and digital identity [...] [Integrating the real or physical identity and the virtual or digital identity is viewed as a solution to this paint point or problem. But it is also an essential element of the original and unique, characteristic artistic expression represented with our iconic OS created by C.S., as can be seen on the webpages Overview and Caliber/Calibre of the website of our OS OntoLinux.]",
"The Fourth Industrial Revolution fuses the physical and digital worlds while revolutionizing the way global leaders think about
security and global connectivity. [The fusion of physical and digital worlds is already an essential element of the original and unique, characteristic artistic expression represented with our iconic OS created by C.S., which is even much more proven with this relation of the Fourth Industrial Revolution or Industry 4.0 and this specific fusion of physical and digital worlds, and the further combination and integration with all the other features of our OS shown in this investigation. Obviously, the World Economic Forum and its partners crossed the white, yellow, or red line in this way and eventually infringed our copyright and other rights.]",
"Beyond automation, the capabilities of advanced technologies such as biometrics and predictive analytics make possible a complete redesign of [...] processes. [This is the next evidence for the infringements of our copyright and other rights, because here we have a causal link with our Ontologic Applications.]",
"[...] focused on three elements [...] [This is another reference to the 3³ Theme of C.S..]",
"[...] redesigning the process to be customer-centric; [See once again the Investigations::Multimedia of the 14th of January 2018 (keyword homocentricism).]",
"Biometric-based [At this point, we would like to give the reminder that the other original and unique work of art titled Ontoscope and also created by C.S. comprises as one manifestation a mobile device that features all kinds of sensors, which can be used for fingerprint scanning and facial recognition for example but also all the other biometric features of a user.]",
Machine learning and AI to improve accuracy [See once again the section Softbionics (SB) of the webpage Terms of the 21st Century.]",
"[...] three distinct intervention concepts [...] [This is one more reference to the 3³ Theme of C.S..]",
"[...] building Known Traveller profile credibility [...] [This point is related to the creation of a virtual or digital identity or a quantified self and its transformation into a qualified self that both are integrated with the real or physical identity. See also once again the case of the Investigations::Multimedia, AI and KM of the 19th of March 2018]",
"Identity verification and access granting with a single-digital token for proof of identity, based on biometrics, for private companies in the travel ecosystem. Once verified, the traveller can use a single token to identify themselves across the ecosystem of partners without a physical ID. [Shown is a graphic with elements that means authentication through biometric verification by taking selfie + fingerprint = mobile phone with protecting app enabling economic transactions. As we already said before, a human-characteristics based (selfie) identity becomes a cybernetic self-image and extension. Also note the aspect of the Economic IDentity (EcoID), which matches the case of the Investigations::Multimedia, AI and KM of the 19th of March 2018.]",
"A digital identity that includes biometric, biographic and travel history data enables the traveller to authorize entities in the traveller journey to access selected information about them to allow for risk-rating, verification and access. [Shown is a graphic with elements that means creation of quantified self over owner in the middle respectively digital identity to enabling activities by qualified self. We also note that this digital identity is presented as a new solution, which implies that our OS is the prior art.]",
"The concept is based on the idea that an individual is in control of providing specific identity information (e.g. biometric, biographic and travel history) to governmental and private-sector players along the journey, such as border control agencies, car rentals, hotels and airlines, for risk-profiling, verification and access [...]. The traveller can select which information is shared for a specific time according to the authority or private entity's requirements to access the services. The identity of the traveller is authenticated through biometric verification and protected by distributed ledger technology and cryptography.",
"The concept is not tied to a particular product, is modular, scalable and based on internationally accepted standards to ensure trust in the technology. [Exactly the same holds for our Ontologic System (OS) and Ontoscope (Os). Furthermore, trustworthiness or credibility, which is also one of the conceptual and essential properties of our OS, as can be seen with the basic properties, the slogan "Stars don't lie", which also constitutes the foundation for Pure Rationality, the reference of the Golden Compass or alethiometer, which is a device that always tells the truth, and has been combined with the Caliber/Calibre and the network of telescopes, which constitutes some kind of a physical and digital distributed consensus integrated in our OS and its ON, OW, and OV. See also the last section of the Investigations::Robotics of the 11th of April 2009, and the Clarification of the 10th of February 2010, 16th of October 2017, and 17th of October 2017.]",
"Exploiting the benefits of ePassports [...] The passport's contactless chip contains biographical data of the passport holder and a digital security feature in the form of a digital signature that seals this data and ensures its integrity and authenticity. Indeed, one of the core benefits of issuing ePassports is to provide border officials with the ability to electronically validate the integrity and authenticity of that document, whether it has been altered and whether or not it has been issued by the right authority. [As we explained before, the information that the correct designation for an epassport is biometric passport and accordingly correct the statement by making clear that the chip contains biometric data but not biographical data, which is a detailed description of a person's life. Furthermore, see once again the section Basic Properties of the webpage Overview for the OS property of (mostly) being validated and verified, and the note "every user gets an ID, that starts with onto#" given in the Feature-List #2.]",
"The Known Traveller Digital Identity concept is designed to enable the voluntary sharing of information whereby the individual builds up trust in their digital identity. To build a trusted "Known Traveller" status, travellers need attestations - authenticated claims as declared by a trusted entity - to be added to their Known Traveller Digital Identity each time a trusted entity - such as a post office or a governmental or educational institution - verifies a claim. In this concept, these attestations are the backbone of trust and the basis of reputation and, ultimately, how security decisions can be made. [By this description it becomes obvious that this KTDI system is the same system discussed in the Investigations::Multimedia, AI and KM of the 19th of March 2018. Somehow this concordance in relation with the utilized foundational technologies on the one hand and the times of their presentations on the other hand is strange.]",
"[...] travellers will consolidate attestations into a Known Traveller profile and increasingly strengthen their claim to compliance, trust and legitimacy as a traveller. People continue to build the Known Traveller status by acquiring more attestations [...] [This description shows once again that a lifelog or quantified self has become an enabling qualified self.]",
"[...] pre-screened [...] pre-vet[ted ...] [Both activities are predictive and proactive, which leads us once again to the Ontologic Applications.]",
"Personalization [] Ability to adapt [] Ability to predict [See once again the section Basic Properties of the webpage Overview to find the OS property of (mostly) being self-adaptive and the webpage Ontologic Applications.]",
"Emotional needs [This is once again a speech act stealing, as can be seen with the section Integrating Architecture of the webpage Overview and the webpage Ontologic Applications.]",
"[...] the framework demonstrates a shift towards self-control and vendor independence, two important design principles integrated into the Known Traveller Digital Identity concept. [Obviously, our OS paved the way in this relation as well with its foundational Integrating Architecture. See also our Managed Peer-to-Peer (MP2P) approach.]",
"When adopting the Known Traveller Digital Identity concept, authorization to travel to or enter a foreign country will be based on the individual traveller and their assessed level of risk rather than a blanket risk level primarily based on an individual's country of origin. Enabling the individual, when requested and at their own discretion, to share their personal information with selected entities [...] [This is exactly what we have said in relation with the case of the Investigations::Multimedia, AI and KM of the 19th of March 2018 and seen directly in this case as well: The partial lifelog or quantified self enables the owner to become qualified and active, and in this way the quantified self becomes an enabling qualified self, which differs from the original lifelog technique or other techniques and technologies, which are relevant in this case, and therefore provides another causal link with our OS, because this extension of the lifelog technique respectively the resulting qualified self is also an original and unique, characteristic expression of the works of art titled Ontologic System and Ontoscope, and created by C.S..]",
"While certain components of the identity are established by issuing authorities (i.e. passport number, bank details), the individual must consent to the sharing of their identities and any related data. This is achieved by individuals securely storing their own identity data on their own personal devices [...] [At this point, it has become obvious once again that the combination of a personal mobile device owned by a user and the virtual identity of the user constitutes a cybernetic self-image and extension (of the real identity) of the user, and therefore is an Ontoscope operatied by an Ontologic System.]",
"The technological developments of the Fourth Industrial Revolution have enabled the conceptualization and construction of a Known Traveller Digital Identity concept. [At this point, it has become clear for another time that the discussed KTDI system and similar IDAMSs are based on our OS, because simply said our OS is also the origin and the foundation of the Fourth Industrial Revolution or Industry 4.0.]",
"Digital identity is the unique representation of a subject engaged in an online transaction. A digital identity is always unique in the context of a digital service, but does not necessarily need to uniquely identify the subject in all contexts. In other words, accessing a digital service may not mean that the subject's real-life identity is known. [Indeed, this is correct and important. Even better is the fact that the features of the related Ontologic System Components (OSC) and the IDAMS of our Managed Peer-to-Peer (MP2P) approach already provide the foundational functionality. For example, the 4th ring and assigned ID spaces of the management structure of our ON, OW, and OV (see the Ontonics Further steps of the 10th of July 2017) make the access of a digital service without knowing the real-life identity of a user possible.]",
"The technological developments of the Fourth Industrial Revolution [...] allow "ownership" and management of the many components of an individual's identity to be migrated from management by centralized services to management by individuals themselves. [See for example the list point "[u]ser centric migration of applications and data from one computing machine to another, even from a personal computer to a cell phone, or an automotive media center" of the Feature-List #1, and also the note "every user gets an id, that starts with onto#" and the list point "[p]ersonal World Wide Web-based infrastructure, network, and virtual drive, that supports the user centric migration [...], synchronization [...] of applications and data, and communication [...]" of the Feature-List #2, which was our circumscription of the field of cloud computing at that time. Even better through our Managed Peer-to-Peer (MP2P) approach the ON, OW, and OV provide all types of ownership and management, which can be customized by a user as well.]",
"1. Distributed ledger enables trust in the network without the control of one central authority [...] [Point 1 is given by the basic properties of our OS and its Ontologic System Components (OSC).]",
"3. Biometrics connects the physical with the digital world and ensures legitimate use of identity information [Point 3 is given by with our original and unique Caliber/Calibre as foundation of our Ontologic uniVerse (OV) and the basic properties of our OS. See also the Clarification of the 16th of April 2016 to learn more aspects about the artistical foundations and expressions of our OS.]",
"4. Mobile devices enable the traveller to carry their digital identity and autonomously choose to share it accordingly [Point 4 is given by the already mentioned representation of one of the original and unique, characteristic expression of the works of art titled Ontologics System and Ontoscope, which is their combination, which again has been described by us as a cybernetic self-image and extension of a user or the real identity of a user.]",
"[...] data evolution [...] [This is once again a speech act stealing, as can be seen with our Evolutionary operating system (Evoos) described in The Proposal and the field of Evolutionary Computing (EC) mentioned in the section Softbionics (SB) of the webpage Terms of the 21st Century.]",
"Alternative to the blockchain, a non-blockchain distributed ledger could also fit the principles. For example, R3's Corda has many of the necessary elements for self-sovereign digital identity systems - coordinated workflow, digital signatures and rules about data evolution. Another example is X-Road, the data-exchange layer for information systems of the Estonian government. X-Road creates a technological and organizational environment that enables a secure internet-based data exchange between information systems. [Somehow we have the impression that both solutions were named to mislead the public about the existence of our OS in this way as well. In relation with the content of this statement we would like to give the reminder that a Total Quality Management (TQM) system based on a control loop is listed in the section Basic Properties of the webpage Overview, which is a special kind of workflow. By the way: At first, the Corda platform was described and promoted as a blockchain platform by every entity, including the main developer, but then this classification was rejected by representatives of the R3 consortium with statements like "[They from R3] were never building [a] blockchain" and "[Corda] was never designed to be a traditional blockchain platform". Furthermore, the Bank of Canada and Payments Canada as well as some Canadian chartered banks announced in May 2017 as a result of a year-long trial of R3 consortium's distributed ledger platform, that it will not be adopted at this time for reasons of transaction privacy and scalability. The latter confirms our explanations and remarks about the blockchain technique and blockchain platforms (see the Clarification of the 21st of March 2018).]",
"Essentially, it is a distributed database whereby a blockchain serves as a public ledger that can never be erased or rewritten. Entries can be altered but not deleted from a blockchain-based distributed ledger. [...] The chain is immutable because every new block in the data store also contains a hash of the previous block in the chain. [We note that the KTDI system is essentially a database and a data store (e.g. Log-Structured File System (LSFS) and Content-Addressable Storage (CAS)) based on a chain of blocks with each block being identified by a cryptographic hash, which means that the aspect of the public ledger is less relevant for its classification, and refer once again to the section Basic Properties of the wepage Overview for showing how the public is misled here as well. See also the two comments made to the next quotes, which provide more details. Also important to note is the point that there will be new problems with the introduction of such distributed ledgers and IDAMSs based on them.]",
"Instead of the actual identity data, the blockchain contains pointers to the data. These pointers are related to an identity and stored on the blockchain to allow participants to access the identity data upon authorization. Pointers lead to hubs, which enable secure data sharing, data storage and maintain data integrity. A hub is a data store containing fragments of identity data at a well-known location (in this case, secured databases with identity information could be considered a hub). Each object in a hub is signed by an identity and is accessible via a globally recognized application programming interface format that explicitly maps to semantic data objects. [With the additional explanation that a "[b]lockchain refers to the data structure comprising cryptographically linked data blocks" it becomes obvious that it is some kind of a distributed recipe-based Content-Addressable Storage (CAS). See the Content Addressable Storage Performance Enhancement by Recipe (CASPER), which explains that "[a] recipe for a file is a synopsis of the data in terms of discrete blocks with each block being identified by a cryptographic hash of the contents in the block", while keeping in mind that metadata is data and therefore a recipe is also data stored in a file, which could also be content addressable and have e.g. a root recipe, and the other Peer-to-Peer (P2P) system referenced therein, such as for example the works with the titles A Distributed Anonymous Information Storage and Retrieval System, and A Scalable Content-Addressable Network. Also see once again the OntoLix and OntoLinux Further steps of the 5th of July 2017 and the comments made to the quote before and the quote hereafter. In addition, the common term for what is called a hub is P2P network, like e.g. a file sharing platform. Furthermore, the fact that the described KTDI system is based on semantic data objects and an Application Programming Interface (API) format that explicitly maps to them is an undeniable evidence that proves the causal link with our Ontologic File System (OntoFS) software component of our OS a further time. Eventually, the only item that we have not explicitly listed in relation with our OS is the consensus algorithm, though on the one hand a consensus protocol must not be based on a specific approach and on the other hand it is common sense for experts that a protocol for the cooperation is required anyway, and we also mentioned that a consensus layer is also an important feature of Multi-Agent Systems (MASs), specifically when their act as a group (see the OntoLix and OntoLinux Further steps of the 18th of October 2017). At this point, it is doubtlessly clear that an essential part of our OS has been copied.]",
"The blockchain holds the pointer, which directs the entity to the right place on a hub that is associated with the identity. [We have to repeat the very important fact once again that this is not the P2P network anymore, which is the foundation of a distributed ledger (see once again the Clarification of the 21st of March 2018), but a P2P computing system as used with for example a file sharing platform or the CASPER mentioned in the comment made to the quote before. This emphasizes our finding that in this way the responsible entities have copied a foundational element of the concept and the implementation of our OS based on the fields of File System (FS) and DataBase Management System (DBMS) as well as validation and verification in general, and on the field of CAS in particular after we published the OntoLix and OntoLinux Website update of the 2nd of May 2016, which on the one hand is exactly the same observation we also made in relation with the case of the Investigations::Multimedia, AI and KM of the 19th of March 2018 and on the other hand is strengthened by the other evidences documented in this investigative case, that prove the causal link with our OS and our Os a further time and also how aggressively every content published by us is copied resulting in the many infringements of our rights that go far beyond a copyright infringement.]",
"Figure 10: Visualization of technology [] Agent [] Mobile [This is the next evidence for the copyright infringement, as can be seen easily with the list point agent systems of the section Basic Properties of the webpage Overview, the section Intelligent/Cognitive Agent of the webpage Links to Software, and the OntoBot software component of our OS, and also with mobile devices based on our Ontoscope.]",
"Additionally, smart contracts can add a sophisticated logic [...] [We already discussed the subject matter in the OntoLix and OntoLinux Further steps of the 5th of July 2017 and the Clarification of the 16th of October 2017, and also the OntoLix and OntoLinux Further steps of the 13th of October 2017, and the Ontonics Further steps and Investigations::Multimedia of the 20th of October 2017.]",
"In general, three types of distributed ledger architectures are distinguished: public, consortium and private ledgers. These types vary according to who is allowed to participate in the network, who executes the consensus protocol and who maintains the shared ledger. For the Known Traveller Digital Identity to be self-sovereign, a liberal approach is required to maximize autonomy for the individual. Therefore, a permission-based public ledger is seen as most applicable. Selected trusted nodes will have certain write permissions, but each individual and each entity is allowed to read the distributed ledger, allowing for full transparency. A decision also needs to be made on whether storage of the identity-related data is held on or off the blockchain. Based on the most advanced thinking, storage of identity information off the blockchain is seen to be the most suitable to enable both the required privacy and scalability. [In general, all types of distributed ledger and other safe and secure systems are imaginable and possible, specifically with our OS. The management structure of our ON, OW, and OV has rings and assigned ID spaces, which makes the structuring in different dimensions possible. For example, in one dimension they are arranged along the scale from permissionless to permissioned, which means as closer a ring and ID space is to the core as more private or controlled it is and as more permissions are required. See once again the Ontonics Further steps of the 10th of July 2017, where the quoted explanation has been taken from. For making a descision in relation with a specific system and its dimensions we created our Society for Ontological Performance and Reproduction (SOPR) with its Articles of Association (AoA), comprising Steering Committees and other provisions and regulations. In particular, we do not think that governments will give the control out of their hands in relation with their individual cyber sovereignty, digital border, and central banking system, which should give a first indication what will be possible and realizable at all. This situation is different in relation with the private sectors and the services they provide. Luckily, we are at a position to give such systems the right direction, if required by the supervision of C.S.. Indeed, we already have made some decisions in this respect but will communicate them at a future date due to plagiarisms like the one investigated here. See also our Managed Peer-to-Peer (MP2P) and Castle in the Cloud approaches based on our OS.]",
"Finally, it is necessary to consider the use of smart contracts to enable a granular permission structure. It is currently unclear which parties should have which permissions. [For this matter our OS provides the IDAMS with verified state machines, the management structure of our ON, OW, and OV with its hypergraph-based rings and assigned ID spaces, and other features and functionalities with some of them also explained in relation with for example our OntoCore software component. Eventually, any related decision making is up to the members of the SOPR. See once again the Ontonics Further steps of the 10th of July 2017 to find out that the concept of the granular permission structure has been taken from us and the comment made to the quote before.]",
"Because the pointers are stored on a blockchain, each identity owner may serve as its own root authority - an architecture referred to as decentralized public key infrastructure (DPKI). These pointers achieve global uniqueness without the need for a central registration authority. This comes, unfortunately, at the cost of human memorability. The algorithms capable of generating globally unique identifiers automatically produce random strings of characters that have no human meaning.
This demonstrates the axiom about identifiers known as Zooko's Triangle: "human-meaningful, decentralized, secure - pick any two". A combination of all three is, for now, considered impossible. [Maybe it is impossible, but we consider to exploit the features of the biometric passport or epassport, or/and the (live) biometric data respectively quantified self of an identity owner for this as well. In this way, such IDAMSs even do not require a mobile device but just only an access point to our OS, like for example an Automatic Teller Machine (ATM) operated by a variant of our OS or another suitable system, to provide a owner access to the qualified self or digital identity in a first step. If a person has no epassport, then an alternative can be used as fallback, which for sure can be based on a mobile device respectively Ontoscope.]",
"[...] zero-knowledge proof [...] [Somehow, this reminds us of our Zero Ontology O#, which is even more foundational and general.]",
"This technology [based on features of an end-user device] would, for example, enable face and voice recognition, as well as iris or fingerprint recognition for authentication of the traveller, or a combination of the above, without the need for an external device. [But in relation with such a KTDI IDAMS or comparable system with a qualified self such an end-user device would be a device operated by our OS or/and an Ontoscope (Os).]",
"There are three primary methods of digital authentication: something you know, a password such as a PIN code; something you have, a smartcard like a hardware token generator; and something you are, a biometric such as fingerprints. Other authentication methods include: where you are, geo-location; and how you are interacting, behavioural biometrics, for instance, keystroke dynamics. [We only say Multilingual Multimodal Multiparadigmatic Multimedia User Interface (M⁴UI), Caliber/Calibre, and Ontoscope with all kinds of sensors, as well as cybernetic self-reflection, self-image, or self-portrait.]",
"Biometrics are used to connect the digital identity with the physical world. [With our OS we even go further on this foundation, as can be seen with the Caliber/Calibre and read in the Clarification of the 16th of April 2016 for example.]",
"The introduction of biometric systems for authentication offers the opportunity for travellers to connect their physical identity with their digital identit and verify that an individual who provides a claim to an identity can in fact provide proof of that claim. [With our multimodal OS and Os we are already here since the end of the year 2006. See also the comment made to a quote above where we mentioned to exploit the features of the biometric passport and see all other related comments made in relation with this investigation.]",
"In the future, other biometrics from emerging modalities, including 3D face, DNA, gait and electrocardiogram, show potential as a means of connecting the digital and physical world and enabling a secure and seamless traveller journey. [See the comment made to the quote before.]",
"Biometric authentication technologies are the key to digital transformation in air travel, enhancing the security process and enabling a personalized, seamless flow. They have the possibility to transform our daily lives beyond travel. [See the comments made to the two quotes before.]",
"[...] biometrics-enabled digital identities [...] [As we said before, in relation with such a KTDI IDAMS or comparable system with a qualified self such a biometrics-enabled digital identity is (a part of) the qualified self and therefore an essential element respectively original and unique, characteristic expression of our iconic ontologic works.]",
"In the short term, a mobile interface is seen as the most convenient way to generate private keys, to send public keys to issuers and to hold digital records with the corresponding private key or decentralized identifier. The mobile identity application should give users holistic visibiltiy of their digital identity components and supply an interface through which they can provide them to government and private entities. The mobile interface may receive push messages with requests for consent to share personal information with receivers for any given time. In this respect, the mobile device acts as a user interface to interact with the network. A mobile interface can be anything ranging from a mobile phone to a smart watch to augmented reality glasses. [We only say Ontoscope, which we also created as an access device to the OS, specifically the Ontologic uniVerse (OV), and refer to the webpage Links to Hardware of the website of OntoLinux. Furthermore, we would like to give the hint to take a look at the Ontonics Further steps of the 15th of January 2018 and the Clarification of the 16th of January 2018. In addition, we note the next speech act stealing with the term holistic. And there is one more thing: Bingo!!!]",
"Not every traveller is expected to have a mobile device. Therefore, alternatives should be provided to enable individuals to consent to sharing their information. In addition, there is much variety in the types of mobile interfaces, requiring broad compatibility of the technology behind the concept. Widely used technology standards are most promising if a critical mass of adopters is to be reached. [Remember that our OS is already iconic and therefore a widely used technology standard. Also see the Managed Peer-to-Peer (MP2P) once again and the comments made to the quotes related to the biometric passport.]",
"1. As technologies continuously evolve, how can we ensure that we take these developments into account and make the right choices regarding which technologies are incorporated? [Simply take our OS because we have incorporated evolution of the overall system in its design.]",
"2. Interoperability relies on interchange protocols, data schemas and governance. How might we engage the relevant stakeholders in the ecosystem and come to agreed standards? [Simply take our OS because we have incorporated interoperability of all systems in its design. For example, for the configuration of any feature or/and functionality only a related formal model or ontology is required. Alternatively, a user can show or tell the OS what it should do. Last but not least, our OS has been designed in such a way that it is able to learn and adapt any system without any prior knowledge.]",
"3. How do we ensure General Data Protection Regulation (GDPR) compliance? Are current cryptographic expression mechanisms up to the task? ["The General Data Protection Regulation (GDPR) (EU) 2016/679 is a regulation in EU law on data protection and privacy for all individuals within the European Union, that aims primarily to give control back to citizens and residents over their personal data and to simplify the regulatory environment for international business by unifying the regulation within the EU and addresses the export of personal data outside the EU." Simply use our OS accordingly, and be honest and careful.]",
"4. What does the financial structure for a Known Traveller Digital Identity system look like? Are the right incentives in place to maintain, exploit and adapt the infrastructure for all actors? [Our OS is already in the process of being realized so this question does not makes sense at all, or said in other words, using our OS already has become mandatory to avoid negative alternative choices.]",
"5. What specifications, protocols and implementations of applications, services, packages and libraries that ensure interoperability across systems and providers already exist, and what new aspects may need to be developed? [Simply continue with copying our OS, become a member of our SOPR, and pay the royalties in accordance with the License Model (LM) of the Terms of Service (ToS) of our SOPR.]",
"6. How do we define the contractual arrangements (smart contracts) between parties that are used to add attestations to the digital identity and enable more granular decision-making about access control? [Become a member of our SOPR and participate in the related working groups or Steering Committees. In general, every member is allowed to file a smart contract but also to demand a deletion. If it makes sense and is validated and formally verified then it will be issued on the distributed system by the related working group or Steering Committee.]",
"[...] core technology capabilities [...] [Do not confuse this term with our Trusted Computing Base (TCB), comprising our validated, verified, capability-based, or/and smart contract-based operating system (kernel) architecture respectively software components, as used for our operating system (kernel) OntoCore or an operating system based on the OntoL4 microkernel or OntoS1 microkernel of our OS, which also provide the foundations for our OntoNet, OntoWeb, and OntoVerse, as well as OntoLedger and OntoLogger software components, and eventually the IDAMS of our ON, OW, and OV.]",
"[...] Traveller downloads the application and creates a digital identity profile in the application; this requires biographic and biometric information. [Here we are again at the beginning of this investigation that is about the transformation of a partial lifelog, digital chronicle, or journal of a person's life, or a quantified self to a cybernetic self-image or a cybernetic augmentation and extension, or a qualified self.]",
"While the concept assumes that a global interoperable system for passenger-controlled digital identities will have a positive effect on security in cross-border travel, it will remain a vision unless it is designed and developed to be adopted at scale. [As we said before, the implementation of our OS in the large scale is going on and its adoption as well as the membership in our SOPR have become mandatory already.]",
"Technology companies have made major strides in data mining, machine learning and artificial intelligence enabling enhanced predictive analytics. [See once again the section Softbionics (SB) and the Ontologic Applications to find out where this has been copied from the material presented before in relation with our OS.]",
"To enable a scaling up, it is critical to exploit network effects and broaden applications of the concept to entice not only travellers but also the public and private sectors to opt in. [We simply say ON, OW, and OV, and also SOPR.]",
"A Known Traveller Digital Identity shows great potential for use beyond travel, such as in healthcare, education, banking, humanitarian aid and voting. To raise the concept beyond occasional cross-border travel, the pilot must exploit the network effects associated with the platform economy and highlight to users the potential broad range of everyday applications. [We simply say ON, OW, and OV, and also SOPR.]",
"The Forum has recently embarked on an initiative in partnership with Accenture to develop a framework for digital identity for use beyond travel and takes into consideration the digital identities of people as well as inanimate objects and entities. [This means nothing else than that they are expanding their fraud in relation with our iconic OS by incorporating the fields of the CPS, IoT, and NES, or being more precise, our fields of the CPS 2.0, IoT 2.0, and NES 2.0, including the Industry 4.0.]",
"Decentralized Identity Foundation (DIF) is an open-source decentralized identity ecosystem that equips the decentralized identity community with the protocols, tools and implementations necessary to create and validate identity attestation. DIF furthers the ability of people, organizations and machines to have a single identifier akin to today's DNS entries for computers. Part of DIF's work is to solve the "last mile" problem of associating the identifier with the human (or similar characteristics of a thing). With these capabilities, users of blockchain-based systems will interact as a single, consistent identity to which all their activity (value and information) will be linked and indexed. Users will have control over who gets to access their information through granular access control for each piece of information. [This is just another attempt of very well known companies to copy essential elements of our OS and our Os, such as the qualified self but also the CPS 2.0, IoT 2.0, and NES 2.0, including the Industry 4.0. But why is it mentioned at all if it already provides foundational functionalities that match the ones of the presented KTDI system?]", and
"The emergence of artificial intelligence and machine learning extends the opportunities to benefit from individual identity information. [As we said several times here and elsewhere virtually everything is included in our OS, as it is also the case with the field of Softbionics (SB). With this statement we get the prove once again that our OS must be the prior art. Besides this, the term emergence used in relation with Artificial Intelligence (AI) and Machine Learning (ML) in this context constitutes the next speech act stealing.]"
This special type of system is basically the same system discussed in the Investigations::Multimedia, AI and KM of the 19th of March 2018 and therefore suffers from the same legal issues. Creating the secure, portable, digital, verifiable, validated and verified, universal, economic, and human-characteristics based (selfie), as well as proof-carrying identity by making a partial lifelog, digital chronicle, or journal of a person's life that includes relationships [and] records of a variety of transactions, including remote purchases, funded wallets, term purchases, cash disbursements, property records, health records, education records, and credit histories among others, which makes it a qualified self-image by qualifying the owner of such an identity, and eventually an essential part of the works of art titled Ontologic System and Ontoscope, and created by C.S.. In the case of a KTDI system we have some identical records, including "information about [her/]his identity [(biometric or human-characteristics based (selfie) identity)], residence and even education [(education records)]. The [mobile device] app could also be used to carry information about the countries a person has visited previously, his vaccination status [(health records)] and even the names and identities of people they are traveling with [(relationships)]". Read the epilog of the Investigations::Multimedia, AI and KM of the 19th of March 2018 once again to find out that we do not claim for an electronic passport based on biometrics but for the overall composition of such a cybernetic system without the "lack of integration between [real or] physical and [virtual or] digital identity".
Indeed, the report
- is in large parts an editing of our original materials and the argument could be that it is only a legal reproduction of our OS in accordance with the Articles of Association (AoA) and Terms of Service (ToS) of our SOPR and
- has a high quality and could very well serve as a foundation for reaching consensus in relation with the harmonization of the overall IDAMS of our ON, OW, and OV with independent subject matter, like for example the issues of cyber sovereignty, other IDAMSs (e.g. Economic IDentity (EcoID) and Known Traveller Digital Identity (KTDI)), and Advance Passenger Information Systems (APISs), though we note that in the moment no content from us was available the quality vanishes.
But
- the preliminary AoA also says that it is not allowed to threaten the integrity of our SOPR, which is doubtlessly the case here, and
- it cannot make us forget the fact, that in the last years the World Economic Forum and its supporters and participants conducted measures to mislead the public about our existence and the true origin of our works and achievements, as shown in this investigative once again.
Like in the case of some open source software, we will not tolerate any
Accordingly, all interested or/and concerned entities, including governments, have to talk with us and only with us, which means at this time our business unit Ontonics and in the near future the members of our SOPR, but not with for example the World Economy Forum, Berners-Lee's World Wide Web Foundation, universities and other research institutes, service providers, or any other entity that has no legitimation and disposition at all in relation with our original and unique, copyrighted works of art, which are required as conceptual and technical foundation for such IDAMSs, other systems, and products and services based on it, obviously and doubtlessly. We highly recommend not to fall in and build confidence on such bold and even criminal activities.
26.March.2018
Ontonics Further steps
While finalizing and updating the Investigations::Multimedia, AI and KM of the 19th and 24th of March 2018, it has become apparent that eventually the promoted Economic IDentity (EcoID) system and Known Traveller Digital Indentity (KTDI) system, as well as similar and alternative IDentity and Access Management Systems (IDAMSs) are rooted in the citizenship government, which is the identity verifier and also the entity that issues the passport, which again is in most countries the biometric passport or epassport already. But
- IDAMS of our iconic Ontologic System (OS),
- management structure of our Ontologic Net (ON), Ontologic Web (OW), and Ontologic uniVerse (OV) of our OS, and
- access devices for the ON, OW, and OV based on or derived from our iconic Ontoscope (Os)
would be advantageous, because we are able to handle
- related to the creation of the OS and Os, and
- protected by international rights
and
in a legal, harmonious, and advantageous way, as we mentioned and suggested in the case of the Investigations::Multimedia, AI and KM of the 24th of March 2018 as well.
Accordingly, we have taken the qualified self, cybernetic self-image and extension, as adapted for the EcoID and KTDI systems, and extended the biometric passport with the related features of our OS, specifically the IDAMS of our Managed Peer-to-Peer (MP2P) approach and ON, OW, and OV, to the Ontologic IDentity (OID or OntoID) and Decentralized ID (DID or DecID) onto# of an IDAMS, which could be based on a digital ledger in the sense of a distributed passport.
For sure, this has implications for everything related.
SOPR #114 Preview
The upcoming issue SOPR #114 (maybe end of the week) will include the following topics and more details about them:
- there will be no cold expropriation by any government,
- SOPR will keep its domiciliary right and hence remain some kind of a gatekeeper managing in a similar way as done with the
- rings and ID spaces in relation with national ID spaces (see for example Managed Peer-to-Peer (MP2P) once again) and
- Ontologic Financial System (OFinS) (see the issue SOPR #113 of the 18th of March 2018),
- flexibility,
- permissionless public over permissioned public or consortium to permissioned private,
- legal issues,
- social,
- media and press (not the free and wild one banned to the 5th and 6th rings),
- digital payment,
- digital map,
- online advertisement,
- big data analytics,
15:34 UTC+2
Topsy-turvy
The case of Orcale vs. Google took the next stage. According to reports a court turned the ruling 180 degrees once again. We quote one of them:
"An appeals court said on Tuesday that Google violated copyright laws when it used Oracle's open-source Java software to build the Android platform in 2009.
Tuesday's ruling is the latest development in a [higgledy-piggledy] eight-year battle between Google and Oracle.
Oracle first brought its case against Google in 2010, claiming that Android infringes two patents that Oracle holds on its Java software, a ubiquitous programming language powering everything from phones to websites.
In 2012, a jury determined that Java does not deserve protection under copyright law.
[In 2014], an appeals court overturned the ruling, raising the question of whether Google's use of Oracle's [Application Programming Interface (]API[)] violated copyright law.
[In 2016 a] jury determined [...] that Google's use of Oracle's APIs was legal under the copyright law's fair use doctrine, which allows the free use of copyrighted material under specific circumstances. Oracle appealed the decision, and a judge took its side on Tuesday.
"There is nothing fair about taking a copyrighted work verbatim and using it for the same purpose and function as the original in a competing platform," a panel of three Federal Circuit judges wrote in Tuesday's opinion.
Oracle said in a statement on Tuesday that the recent "decision protects creators and consumers."
[...]
Google isn't the only company that stands to lose from this decision. Many others rely on open-source software to develop their own platforms. Tuesday's ruling means that some will either have pay to license certain software or develop their own from scratch.
"The decision is going to create a significant shift in how software is developed worldwide," [a commentator] said. "It really means that copyright in this context has teeth."
"Sometimes free is not really free," he added."
Another report also made the subject matter clear:
"APIs have always fallen under copyright, but just because you have something copyrightable does not mean you will ever assert it successfully. In US copyright law, the creative expression is what's copyrightable. You can attempt to assert copyright over a few words [...] but if it's not a substantial and original expression, you'll fail.
[...]
So Oracle was on firm ground, as Java ticked the boxes required: it was, to use the technical terms, an original work of authorship fixed in a tangible medium of expression.
[...]
As the Federal Court notes in its judgement, Google had a high hurdle to cross: "Because fair use is an affirmative defense to a claim of infringement, Google bears the burden to prove that the statutory factors weigh in its favor.""
Obviously, in the cases of the works of art titled Ontologic System and Ontoscope, and created by C.S. we even have much more original and unique, creative works than an Object-Oriented (OO 1) programming language for distributed computing, and to make it short we knew that they would be taken by all industrial companies affected, so we published it in a way that also addresses all these 4 factors in a way that weigh in favour for us, for example by
as we explained and discussed several times in the last years (see for example the Clarification of the 7th of November 2016). :D
Hopefully, we do not need to explain why our legal situation and standpoint have been strengthened tremendously and improved significantly with the latest ruling, because on the one hand even the interface is not free, as we always argued in general but had to accept by the ruling of 2016 in particular (see also the discussion API free or not free? published on the 16th of December 2016), and on the other hand the same legal point of view can also be applied on descriptions, models, and architectures of systems.
At this moment, we do not think that this ruling has any effect on the Terms of Service (ToS) with the License Model (LM) of our Society for Ontological Performance and Reproduction (SOPR), but it makes it very much easier for us to push them through, or as we said some days ago already: Membership in our SOPR has become mandatory for avoiding the negative alternatives.
Needless to say, we are continuing with the definiton of our LM in relation with open source hardware and software, because the social aspect of such activities should not be blocked. But the actual legal practice is not sustainable, so to say.
In this relation, we also came back to the issue related to deep learning systems and might found the right arguments (once again) by focusing on the composition of the
as already discussed in the Website review of the 2nd of February 2018 and related publications.
Furthermore, the company Oracle owes us a huge amount of royalties for the part of our original and unique, iconic work of art titled Ontologic System and its Ontologic System Architecture that is related to our Ontologic File System, indeed, or the admin-free database will become a common relational database again (see its case in the Investigations::Multimedia, AI and KM of 24th of February 2018). There is neither a loophole, for example based on the copyright law's fair use doctrine nor a cherry picking for Oracle as well.
Thank you very much for this legal processing. :D
30.March.2018
OntoLix and OntoLinux Further steps
We worked on our OntoLedger software component, played around with the foundations of our IDentity and Access Management System (IDAMS) architecture based on the mathematical structure hypergraph among other elements and used for our Ontologic Net (ON), Ontologic Web (OW), and Ontologic uniVerse (OV), and improved a basic IDAMS architecture based on the blockchain technique.
Ontologic Net Further steps
We worked on the IDentity and Access Management System (IDAMS) of our Ontologic Net (ON).
We also added a basic service.
Ontologic Web Further steps
We worked on the IDentity and Access Management System (IDAMS) of our Ontologic Web (OW).
We also added some new basic services and integrated them with the existing service platform of our
Ontologic uniVerse Further steps
We worked on the IDentity and Access Management System (IDAMS) of our Ontologic uniVerse (OV).
31.March.2018
Ontologic Web Further steps
We worked on the IDentity and Access Management System (IDAMS) of our Ontologic Web (OW).
We also added some new basic services and integrated them with the existing service platform of our Ontologic Financial System (OFinS).